Penetration testing applications
Related Case Studies


Kerena Age: 20. London - Paris - Milan - Rome - Maldives, Singapore, Hong-Kong, Bali, Japan, UAE, Geneva, Zurich, Barcelona, Madrid, Marbella, Ibiza, Greece, Mykonos, Athens, New York, California, Las Vegas, Miami, CaribianI have very spontaneous and adventure character, i love to enjoy my life in every way.


Hi guys Virginia Age: 23. Hi sexy ! My name is Sophie and I'm a hot busty milf in the Secaucus area for a short time! I am looking for mature, generous gentlemen to spoilI can do Top, Bottom, Switch, Men, Women, or Couples
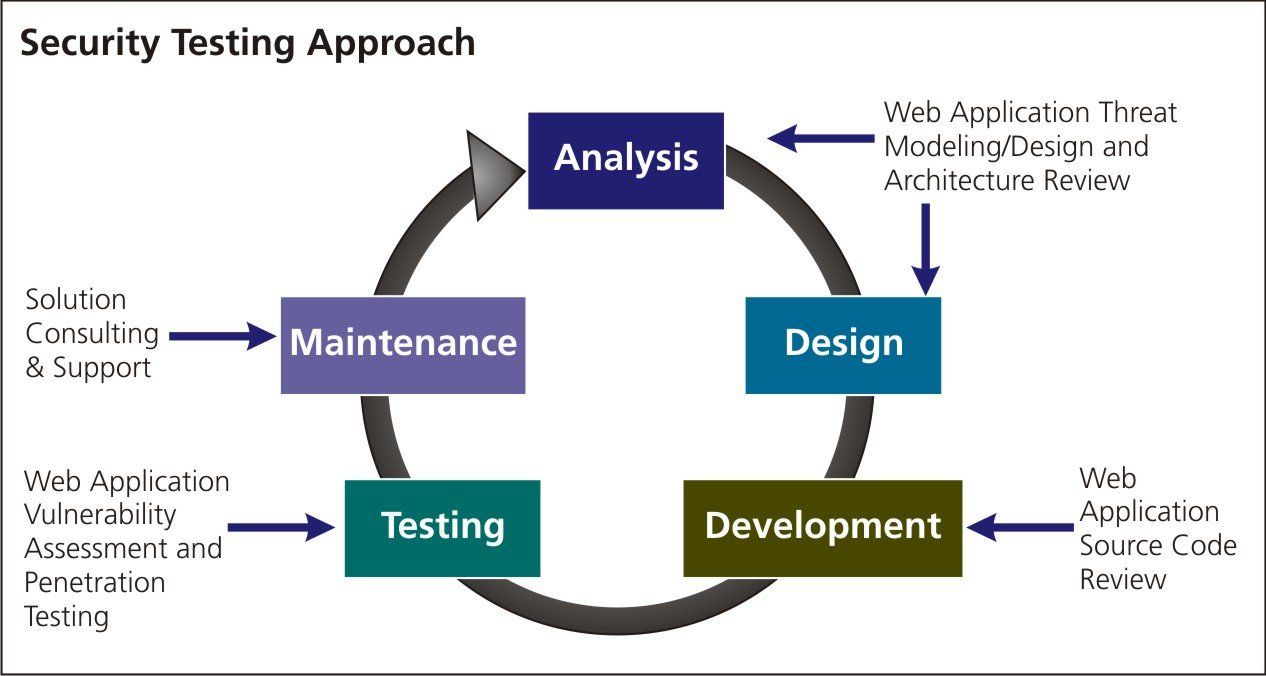
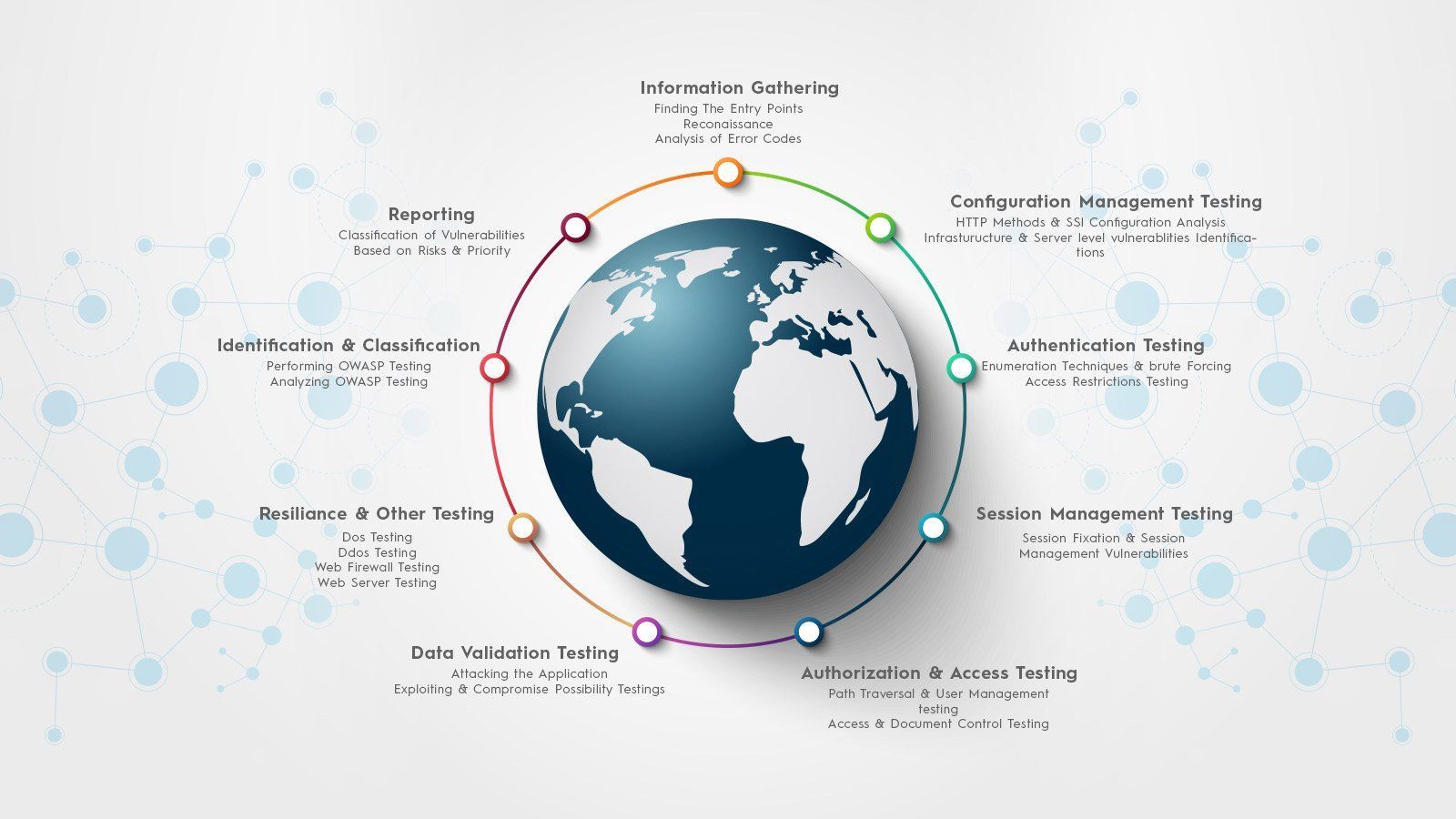
Information Gathering

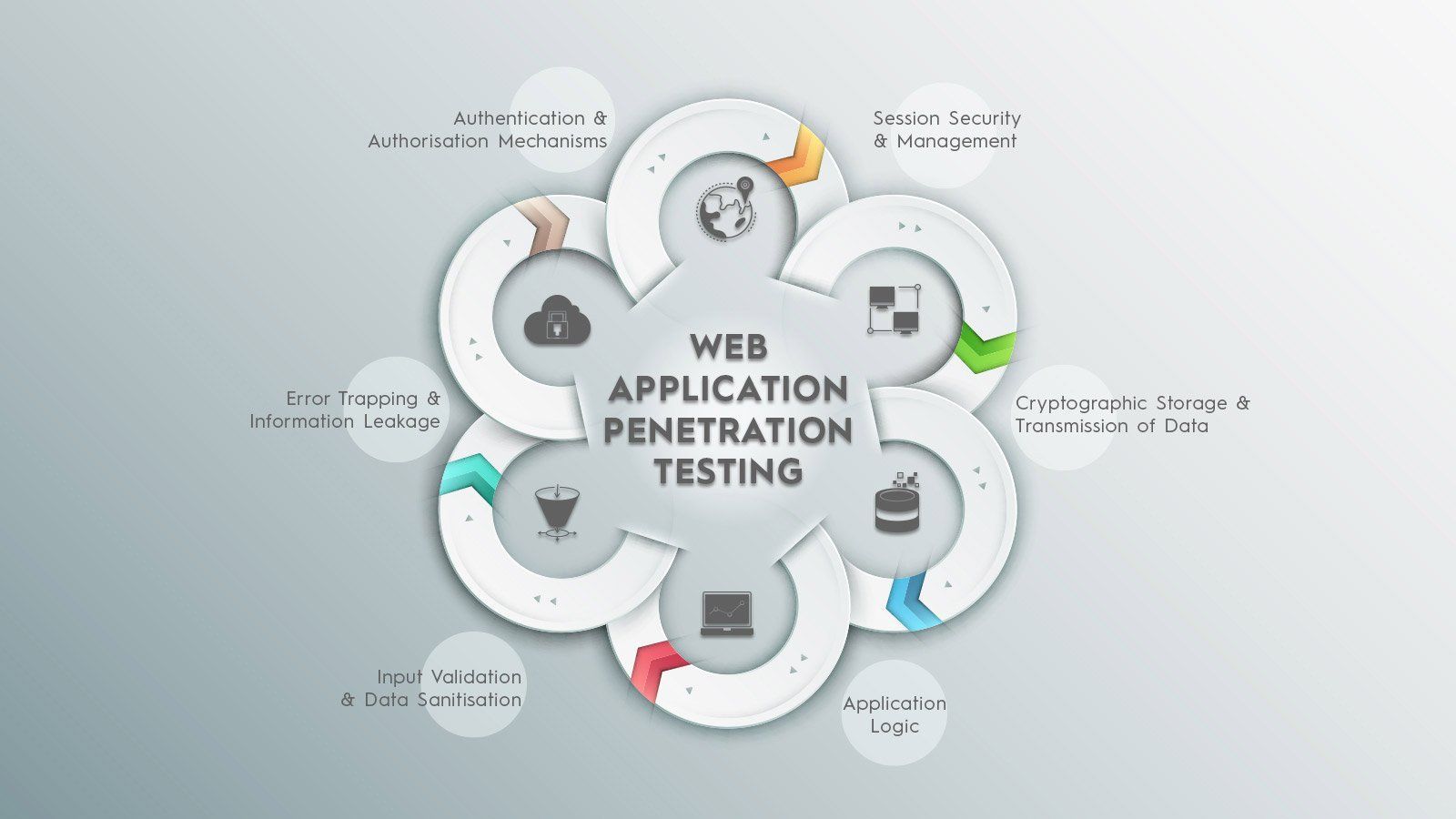
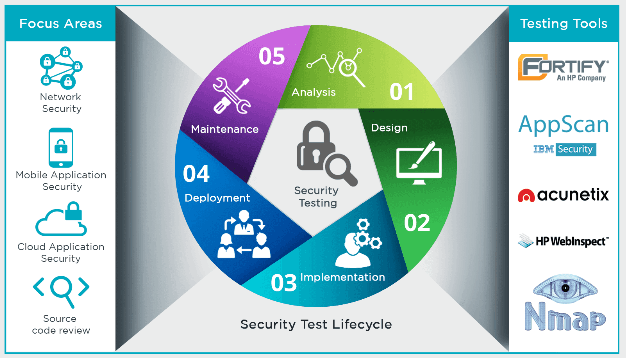
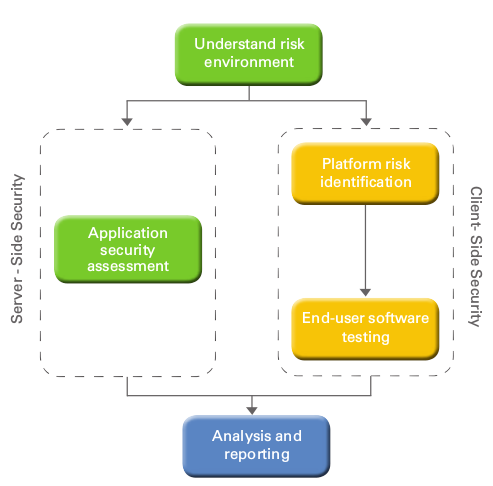
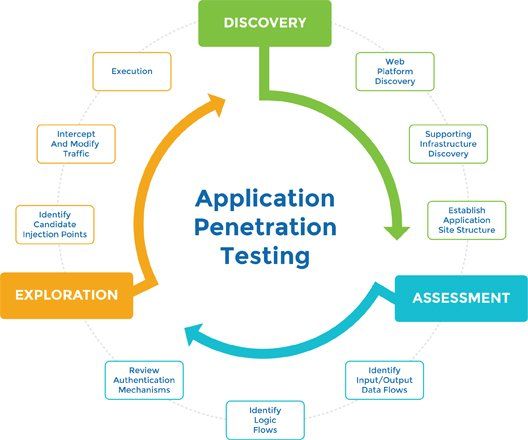
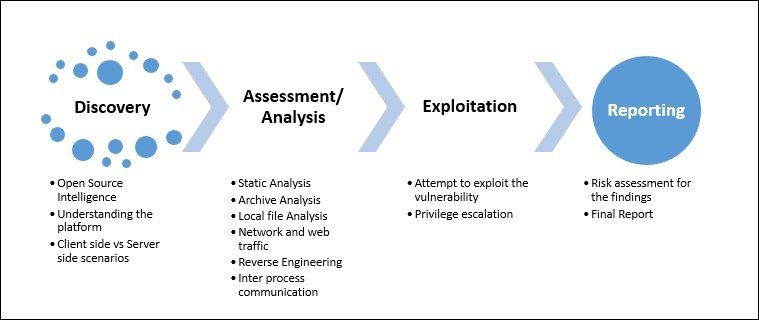
Applications are one of the most significant points of vulnerability!In today's technology-driven world, institutions have become critically dependent on.
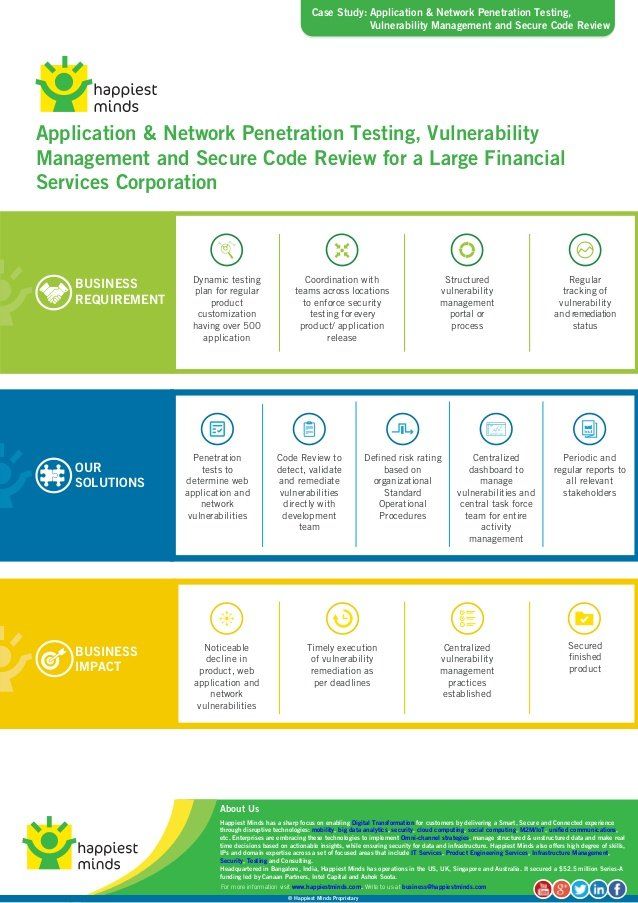

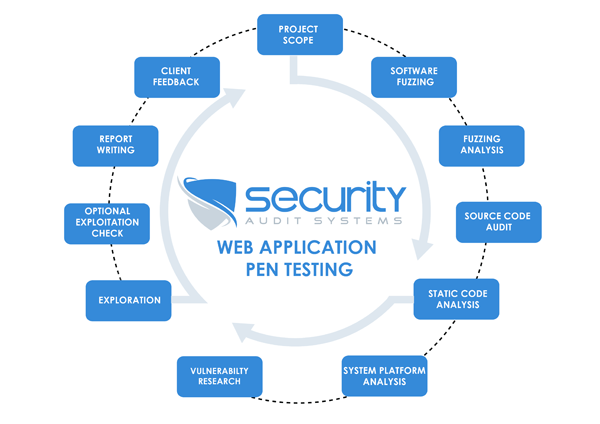

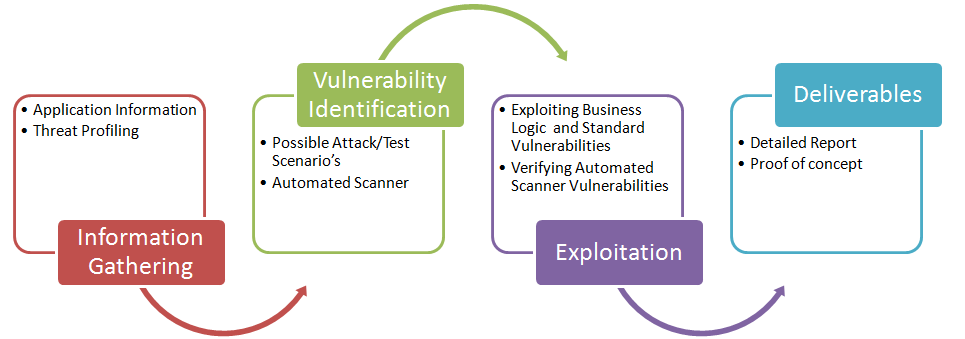


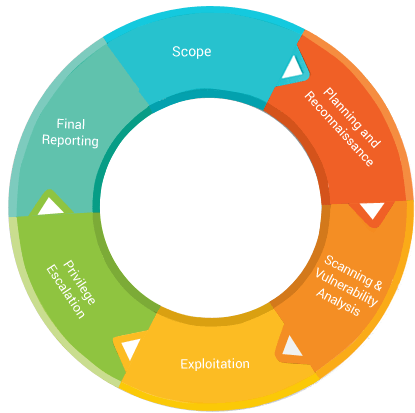
Description:If session tokens are not sufficiently random it opens the door to session hijacking attacks, and should be noted. Each one has a different attack vector. Some of these techniques involve testing approaches similar to those used in the OWASP testing guide. I bookmarked your site and it is in my favorites. Once the testing scope is set, vulnerabilities are identified and exploited to open up potential pivots to other devices that may have been considered secure. Regardless of the type of testing, each engagement combines the use of automated tools with hands-on analysis by qualified engineers to produce a detailed, risk-based report with actionable recommendations for mitigation.










































User Comments 1
Post a comment
Comment: